I am going to share with you all possible ways to hack admin or administrator account in windows XP. Today i will explain how to hack admin or administrator account in just 2 minutes. So guys get ready to hack your friends systems in 2 minutes.
Most of times specially in our college we don't have the access to the admin account, now suppose you want to install a software on that system. What you will do now? Ask the admin to enter the password for you or simply hack it by yourself. I will tell you frankly that i have never opted method one in my life. Whenever i need administrator right i have hacked it but guys don't do it like that ways because i got suspended from lab twice for doing that.
There are four ways to hack the admin password:
1. Simply accessing Unprotected Administrator Account.
2. Hacking Through Net User Command.
3. Hacking Using the ERD(Emergency Rescue Disk) Commander.
4. Resetting admin password using Ubuntu Live CD or DVD.
Lets start from the first technique to hack the admin or administrator password..
1. Simply Accessing the Unprotected Admin or Administrator account.
How this hack works ? When we install windows XP on our system we usually rename the username as our name or some other keyword. But windows always creates the administrator account whenever we set up windows XP. So when you create your user account during install , windows creates two accounts that is one is your username account and other is Administrator account. But the main thing is that you will only see the account with your username and the Administrator account is hidden but its there and you can easily access that using the following steps:
Step1: Start your computer.
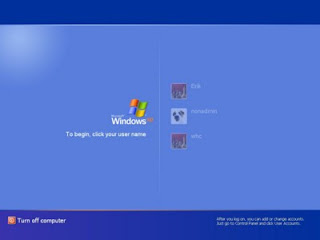
Step2: Now let it start until the windows user's username appears as shown in snapshot below...
Step3: As This Window Appears Press Ctrl+Alt +Delete (2 times).. Now the Windows like shown below appears..
Step4: Now as shown above Enter the Administrator on the Username box and press enter... Now you will be login in the admin account can easily rest the password...
For Resetting password you can follow two Procedures..
Procedure 1: Goto Start --> Control Panel --> User Accounts.. Now select the account whose password u want to reset.
Procedure 2 : Follow the Next method i.e hacking password through Net User Command.
Note: Hack 1 will only work if Administrator(default) is unsecured i.e User as some other username like above shown figure...
2. Hacking admin or administrator account using net user command
Note: This will work only when user has access of user account or some how he has been allowed or working in admin account.
Steps to hack admin account:
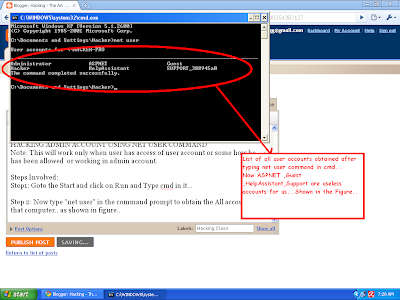
Step1: Goto the Start and click on Run and Type cmd and press enter ...
Step 2: Now type "net user" in the command prompt to obtain the All accounts on that computer.. as shown in figure..
Step 3: Now Select the account Which u want to Reset the Password...
Suppose that we want to Reset the Password of Administrator...
Now Type "net user Administrator * " Without quotes... and press Enter. As shown in the Below Figure..
Step 4: Now after that press Enter Twice to rest the password. Now Next time u open that Account .. It will not require any Password..
3. Hacking admin account using ERD commander (100% working hack)
This hack has no restrictions , using this hack you can hack each and every computer.
First of all Download the ERD(Emergency Rescue Disk) commander... Extract the Files and Make a CD...
STEPS INVOLVED :
1. Insert the ERD Commander Boot CD into the drive and restart the system
2. Boot the computer using ERD Commander Boot CD. You may have to set the boot order in the BIOS first.
3. Select your Windows XP installation from the list as shown.





Steps involved :
2. Boot the computer using ERD Commander Boot CD. You may have to set the boot order in the BIOS first.
3. Select your Windows XP installation from the list as shown.
4. From the ERD Commander menu (Start menu), click System Tools and click Locksmith
5. Click Next
6. Select the administrator account from the list for which you want to reset the password.
7. Type the new password in both the boxes, click Next and click Finish
8 . Restart The System and take the CD out of the Drive..And Enjoy Admin account...
Method 4: Resetting windows password using Ubuntu Live CD or DVD
For this hack you will require the Ubuntu Live CD.Steps involved :
- Insert Ubuntu Live CD and boot from it.
- Open terminal and install chntpw in Ubuntu. To do so use the following commands.
sudo apt-get update
sudo apt-get install chntpw - Now mount your Windows volume. In my case it was dev/sda1. Replace it with yours.
sudo mkdir /media/WINDOWS
sudo mount /dev/sda1 /media/WINDOWS - Now navigate to the Windows configuration folder.
cd /media/WINDOWS/WINDOWS/system32/config/
- To reset the administrator password enter
sudo chntpw SAM
- After completing this command you will see 5 different choices. Select the 1st one and press Enter and its done.
- Now restart your system, it will not ask any password.